Fortigate - Vlans in NAT Mode Lab
The Fortigate Firewall supports VLAN trunk links with IEEE 802.1Q-compliant switches or routers, transporting VLAN-tagged packets between physical subnets or networks. VLAN sub interfaces can be defined on all FortiGate physical interfaces, but access to the physical interfaces on a virtual domain is limited. The FortiGate unit functions as a layer-3 device in NAT mode, controlling packet flow between VLANs and removing VLAN tags from incoming packets. It can forward untagged packets to other networks like the Internet.
This Firewall can tag packets leaving on a VLAN subinterface, remove VLAN tags from incoming packets, and add different VLAN tags to outgoing packets. In VLAN configurations, the fortigate unit can apply different traffic policies, resulting in less network traffic and improved security.
Below is the network Diagram for this lab:-
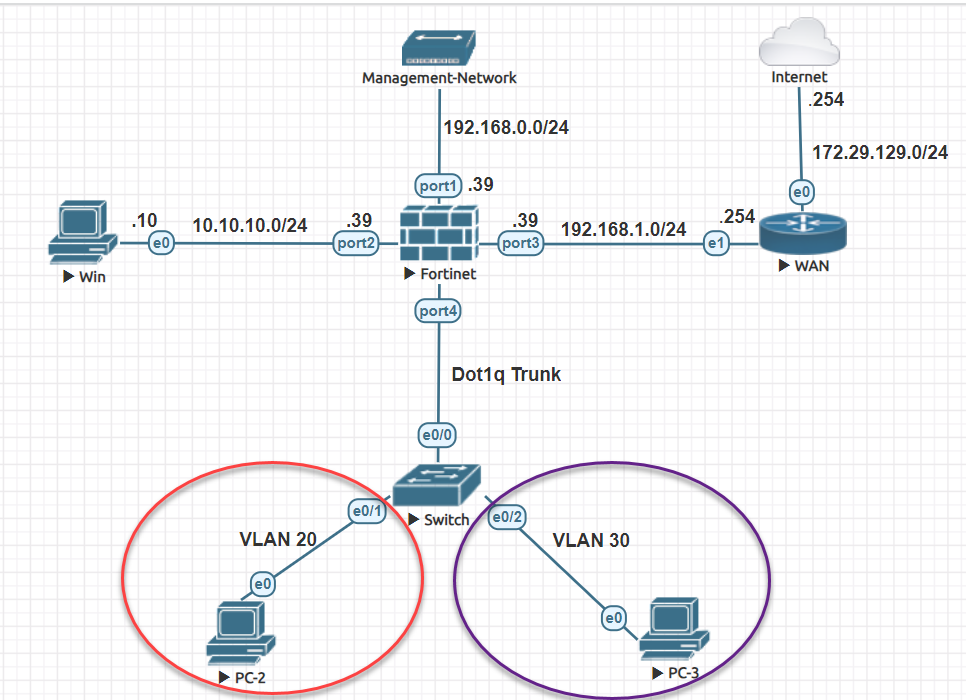
This Lab will include below tasks:-
A) Configure switch interfaces and also Dot1q trunk on Fortigate firewall using port#4 , add vlan interfaces.
B) Configure Firewall Policy to allow internet access for both PC-2 & PC3 (in separate vlan segments)
C) Verification – Check Fortiview Sources, destinations, policy and sessions.
Solution:-
A) Configure switch interfaces and also Dot1q trunk on Fortigate firewall using port#4 , add vlan interfaces.
Cisco switch configuration changes:-
Switch(config)#vlan 20
Switch(config-vlan)#name For-PC2
Switch(config-vlan)#exit
Switch(config)#vlan 30
Switch(config-vlan)#name For-PC3
Switch(config-vlan)#int e0/0
Switch(config-if)#switchport trunk encapsulation dot1q
Switch(config-if)#switchport mode trunk
Switch(config-if)#int e0/1
Switch(config-if)#description "Connected to PC2"
Switch(config-if)#switchport access vlan 20
Switch(config-if)#int e0/2
Switch(config-if)#description "Connected to PC3"
Switch(config-if)#switchport access vlan 30
Switch(config-if)#end
Switch#wr
Fortigate Firewall Configuration changes:-
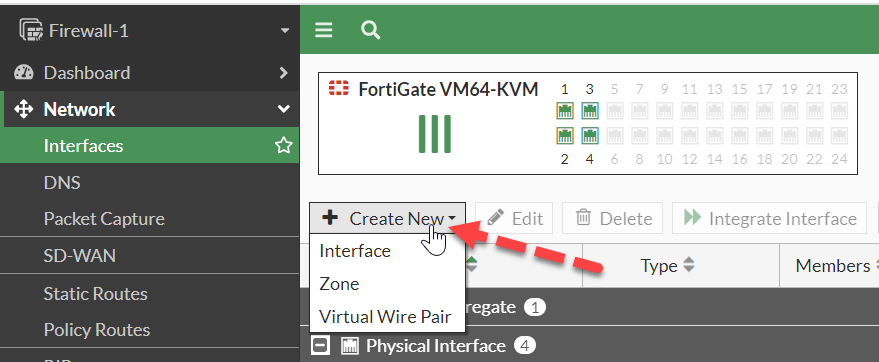
Navigate to the Network menu and select Interfaces to tweak an interface. Click Create New > Interface.
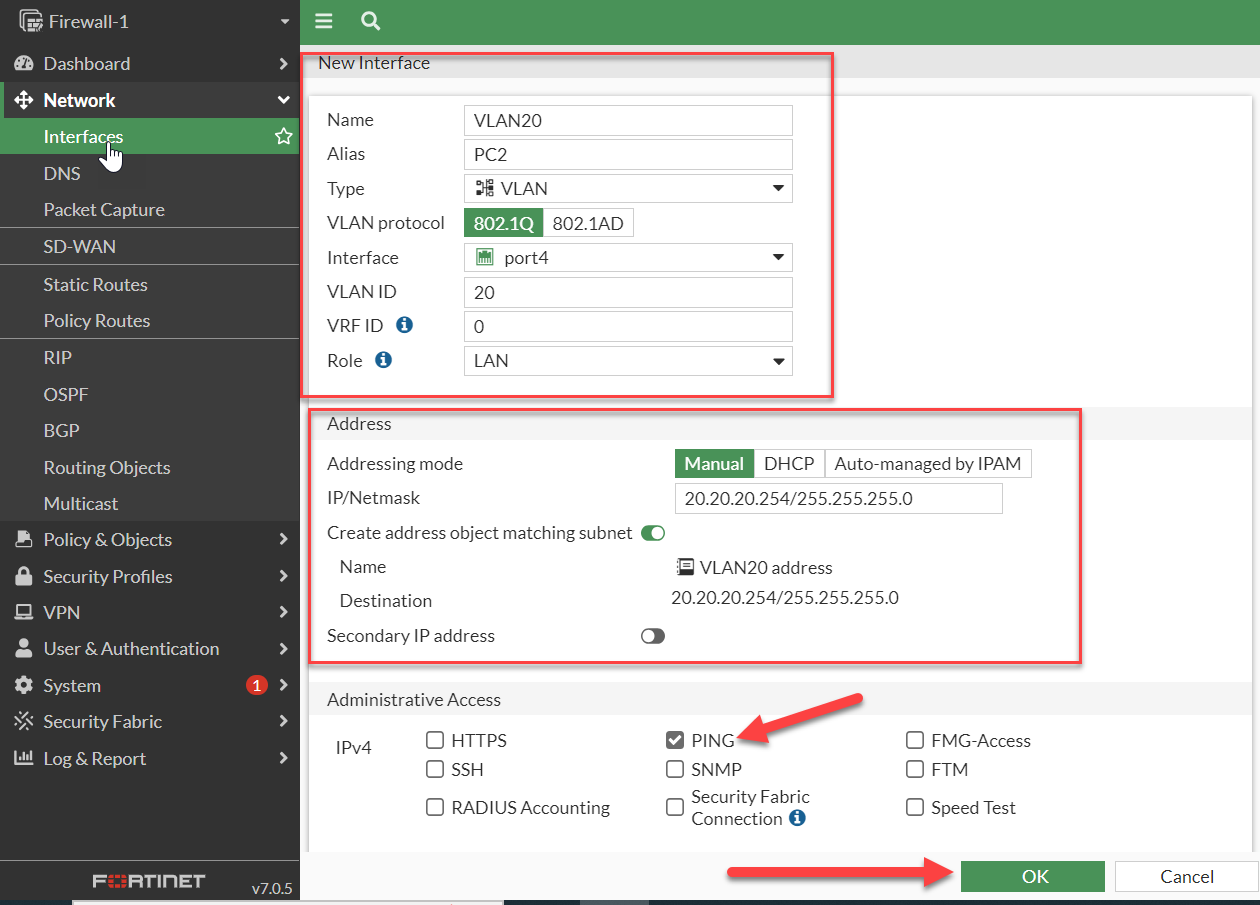
Now, we will configure vlan 20 interface on fortigate:-
Next step is to configure vlan 30 interface on fortigate:-

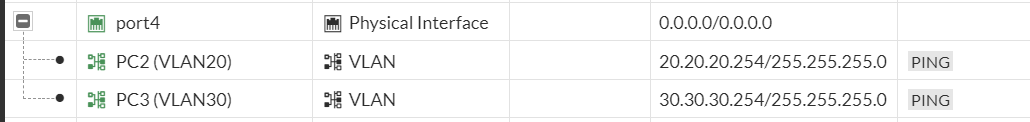
Now we will be able to see two newly created interfaces for VLAN20 and VLAN30 under port#4
B) Configure Firewall Policy to allow internet access for both PC-2 & PC3 (in separate vlan segments)
Here we can create separate policies for both vlan 20 (PC2) and vlan 30 (PC3).To make a new firewall policy, open the Policy & Objects menu, then choose Firewall Policy.

Leave A Comment
Please login here to comment.

Comments