Fortigate Link Redundancy Lab
Only one interface is used by traffic in a redundant interface. This is in contrast to an aggregated interface, in which data travels across all interfaces simultaneously to maximize available bandwidth.
To be eligible for inclusion in a redundant interface, an interface must meet the following criteria:
ü It must be physical and not a VLAN interface.
ü It must not be a part of another aggregated or redundant interface
ü It must be in the same VDOM as the redundant interface.
ü It should not have any VLAN sub interfaces.
ü Nothing in the VIP, security, or multicast policies mentions it.
ü It is not getting monitored by HA.
ü The interface is not a HA heartbeat interface.
ü It's not set up to use Dynamic Host Configuration Protocol (DHCP) or PPPoE and it lacks an IP address.
ü It does not belong to the backplane interfaces of the FortiGate-5000 series.
Below is the network diagram for this lab:-
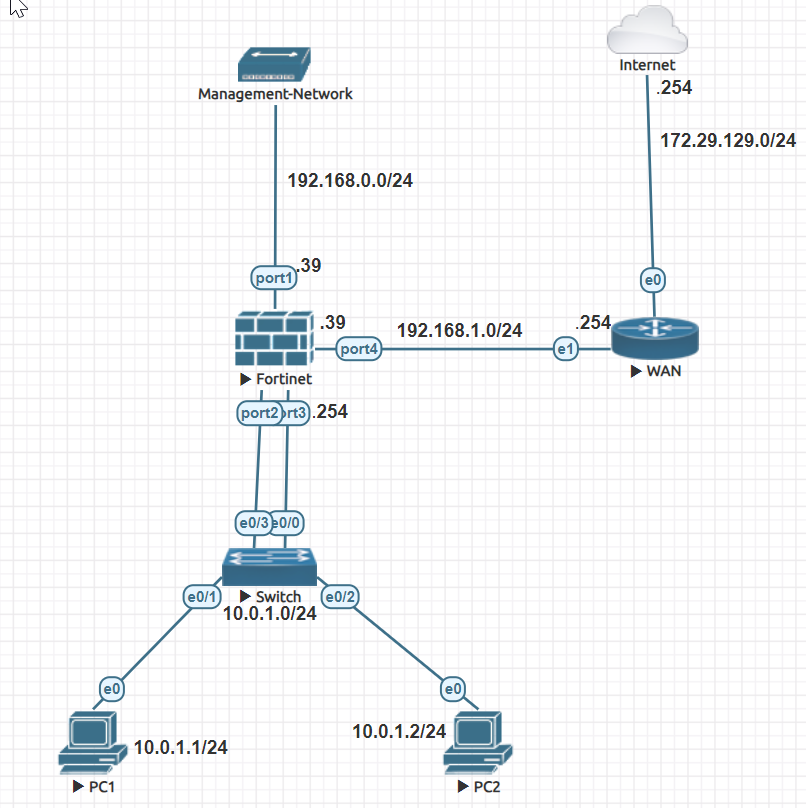
Lab Configuration:
Switch configs:-
Switch(config)#int range e0/0, e0/3
Switch(config-if-range)#switchport trunk encapsulation dot1q
Switch(config-if-range)#switchport mode trunk
Fortigate Firewall initial configuration:-
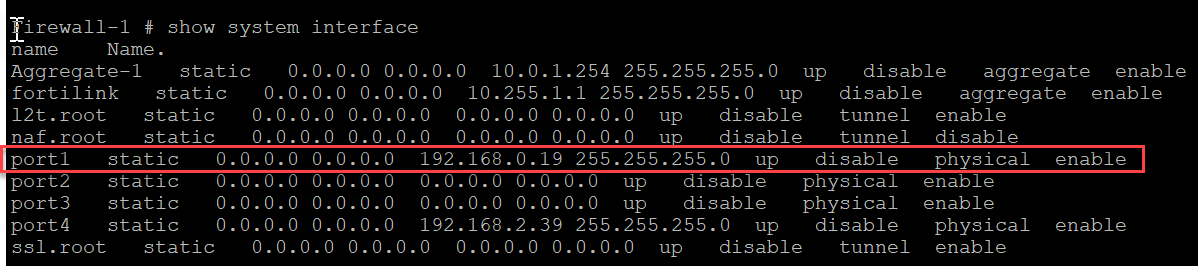
Port1 for Firewall is configured with static IP (192.168.0.19) for management
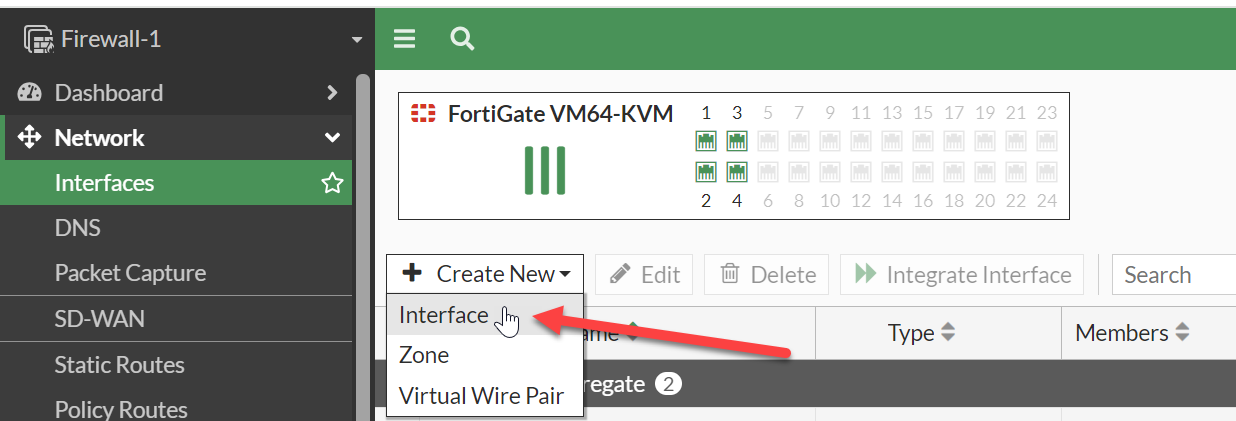
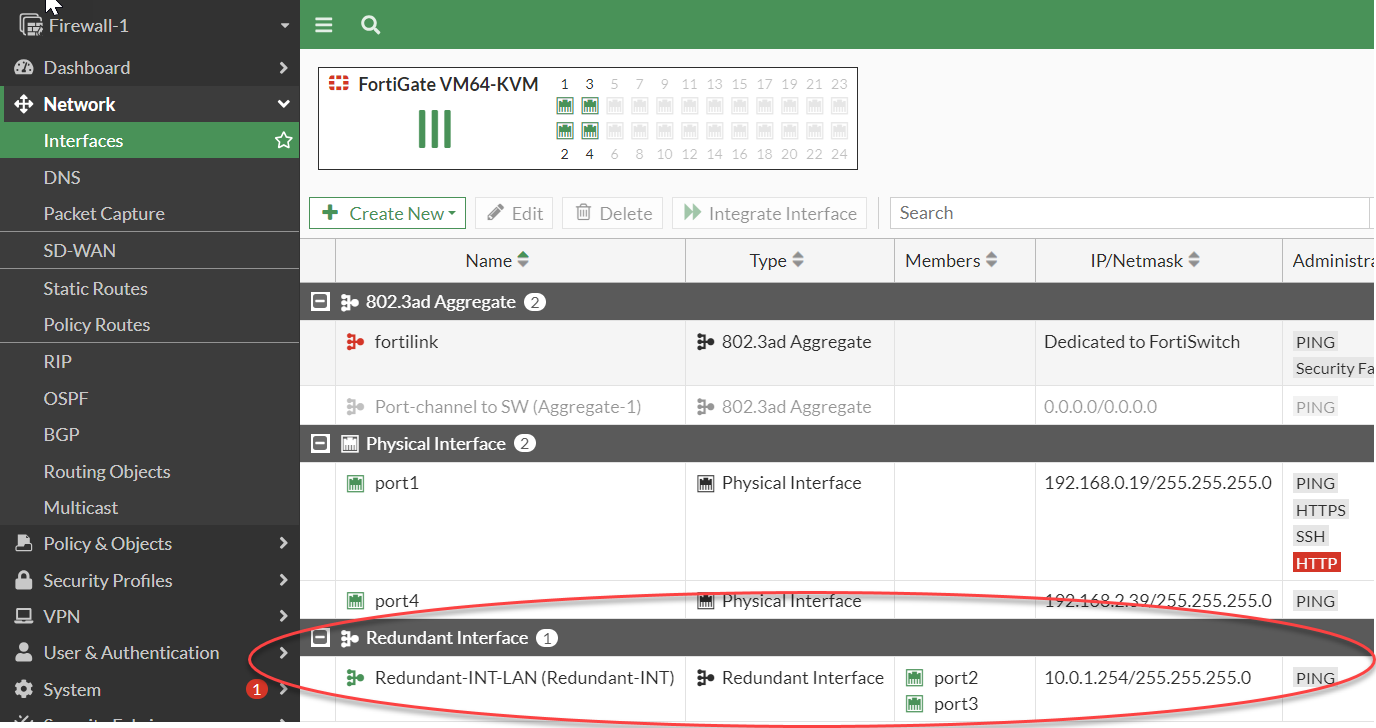
Lets create an interface type “Redundant interface” through GUI, Network > Interfaces is where you can set up an interface. Choose "Create New" then "Interface.":-
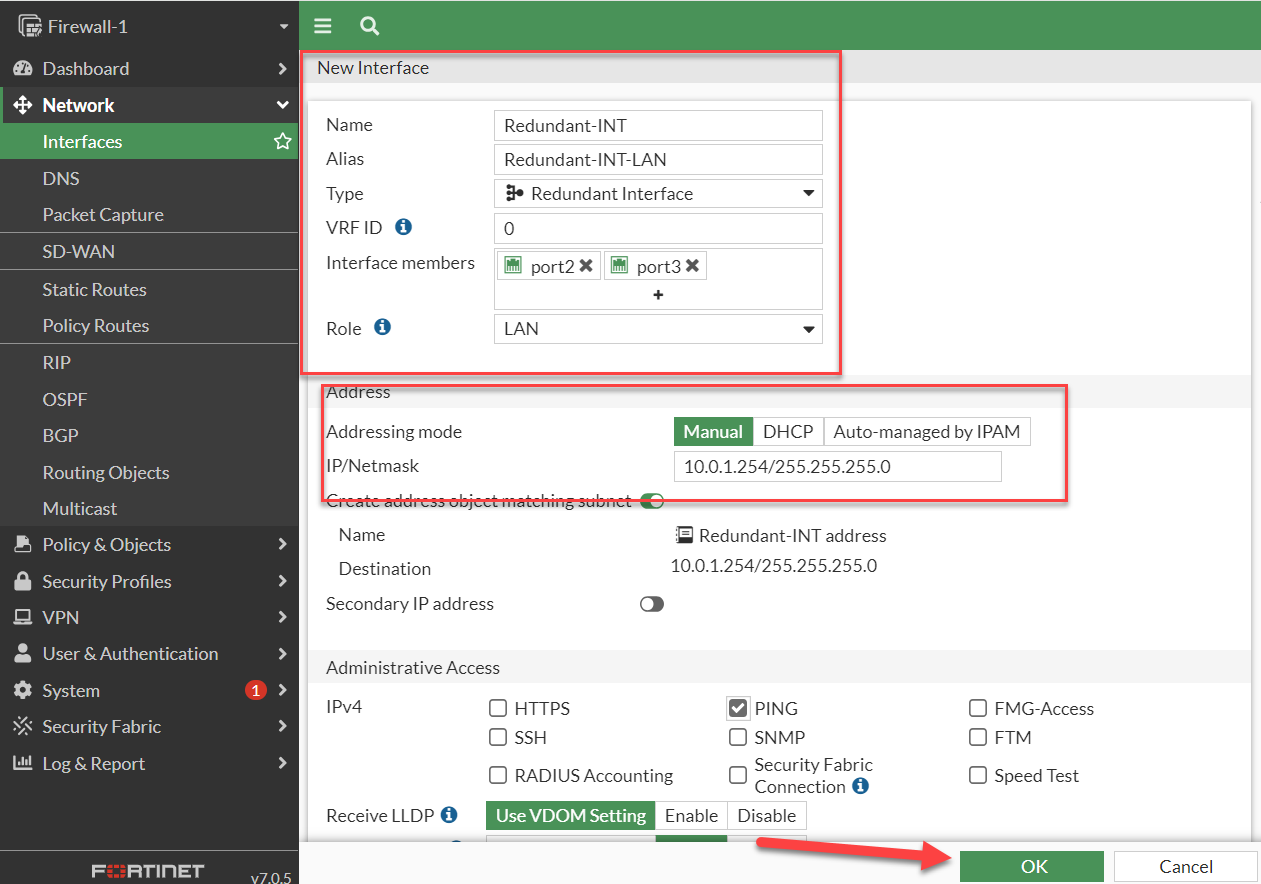
By combining Port2 and Port3, a redundant interface has been set up.
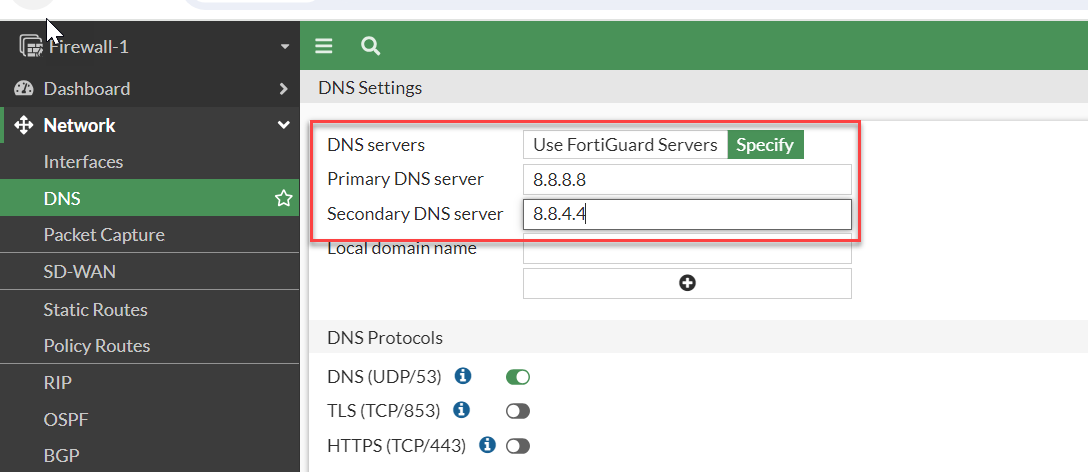
Navigate to the Network menu and then Click on DNS. Adjust DNS Servers to Meet Your Needs, Set up the main and backup DNS servers as required. Select "Apply."
Create a new default route towards the ISP. Port 4 (in this scenario) will be the WAN interface with ip address 192.168.1.39

Leave A Comment
Please login here to comment.

Comments